Article Summaries
- kevcdn – wordpress security
- wpmudev – keeping wordpress secure the ultimate guide
- codeinwp – secure your wordpress website
- makeawebsitehub – wordpress security
- sucuri – how to clean hacked wordpress
These articles offer the same general advice, with a few offering some unique tips. For instance, the Sucuri article deals specifically with a post-hack scenario; though in describing the recommended steps to take, provides more of the same general advice echoed in the other articles. All good information. Aside from basic things like well-chosen passwords, there are more WordPress-specific tips, such as limiting or disabling access to WP files and adding extra login parameters.
Questions and Answers
“How do you harden a WordPress website? Mention at least 10 different settings, techniques, or tricks.”
“To harden a server or application means that you take steps to reduce the attack surface or entry points for attackers. ” (Sucuri) Hardening a WordPress website involves, first, adhering to good security practices (good passwords, updating, etc.), and then taking care to limit any vulnerabilities inherent to WordPress itself. Ten of the most recommended steps are:
- Keep WordPress and plugins up to date.
- Two factor authentication (Google offers a plugin).
- Use security plugins (preferably of the highly-vetted variety).
- Use secure connections (SFTP, SSH, SSL).
- Secure databases with unique passwords and limit access to areas that point to database related information.
- Add extra layers of security to admin login; already mentioned: two factor auth, but also applicable would be limiting login attempts and obfuscating the page.
- Disabling access to wp-config.php, and other WP files which may be openly accessible. Related to this is to redirect/block access to ‘directory’ pages which may point to server structure or WP vulnerabilities.
- Disable file editing (on server and dashboard)). This can make certain activities more difficult, but overall the security benefits should outweigh any inconvenience.
- Use automated backups and maintain a level of redundancy; test recent backups.
- Research plugins thoroughly before installing.
“What plugins/resources are available for WordPress Security? Name at least 5 plugins or resources. Which one do you think you will use and why?”
Of the many available, here are five: Wordfence Security, Sucuri Security, All In One WP Security & Firewall, Plugin Security Scanner, WPS Hide Login.
At the moment I think I will be using at least Sucuri and WPS Hide Login; though I may swap out Sucuri upon further research, if something else seems more efficient/applicable to my use-case. Will also be using Wordfence, it is a plugin which can be installed by default, and I tend to activate it as its features seem simple yet effective.
“What would you do if you were hacked?”
First and foremost is determining the nature of the intrusion; what has been compromised and what vulnerabilities may extend from the already-compromised areas. Beyond that, in terms of securing and cleaning, it would depend on what is discovered from the previous inquiry–but the steps listed on the Sucuri article are all certainly valid. After some level of access has been secured, first steps would be to alter credentials and remove suspicious/altered/potentially-altered files (perhaps via SFTP/SSH).
“What is SSL? How would you activate it in your domain? Submit a screenshot of your activation.”
SSL (Secure Socket Layer) encrypts traffic between the server and browser. On this domain, it can be activated using the cPanel–WordPress installs do offer their own SSL functionality, however, it’s best to have it domain-wide if used at all.
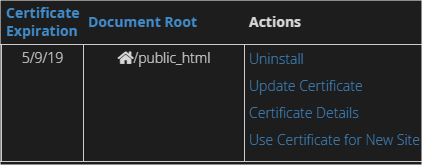
I already had this set up, but I did, now, configure forced SSL.
“Install at least three plugins/resources that you consider the best to secure your testsite for the course and submit screenshots of the setup screen(s).”
I can’t say for sure at this time whether I consider these the “best,” they are simply the ones I’ve researched enough to feel are worthwhile.
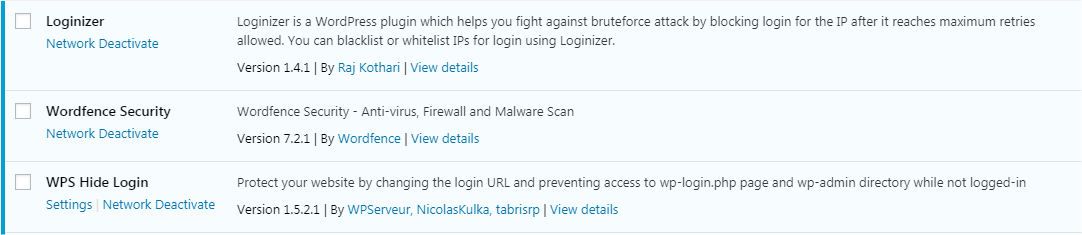
Not shown: Sucuri, as I have not really settled on it as the more ‘robust’ general plugin to use alongside the others shown.
